Video Encryption: Techniques, Components and Challenges
Explore the world of video encryption: Learn about techniques, components, process, and challenges in securing your video content. Stay informed!
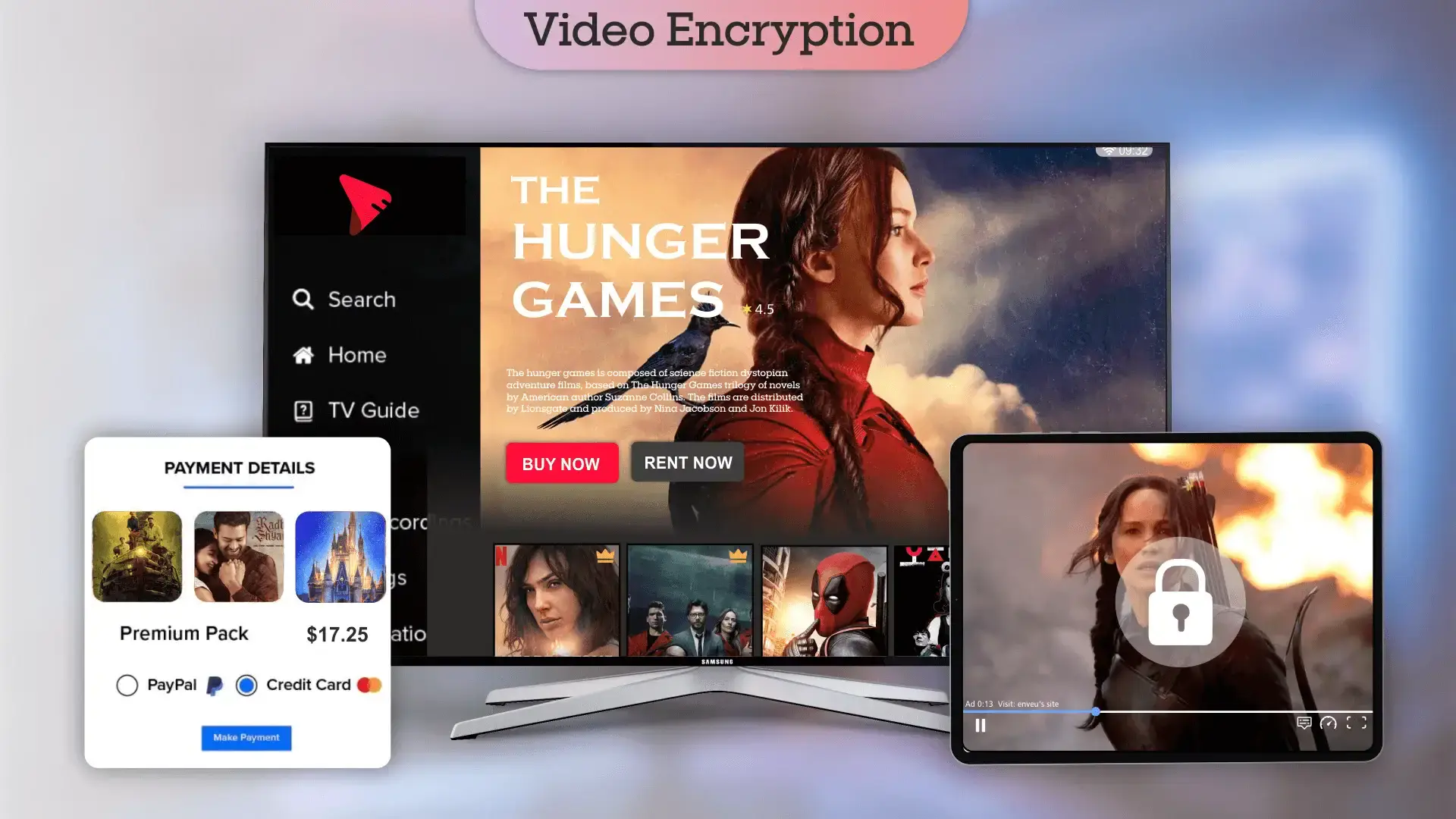
Digital security, no doubt, is a topmost concern for every business owner in today’s technological era. If we talk about online tutorials, streaming services, or the realm of digital marketing, it becomes essential to protect your data’s privacy, integrity and authenticity. It will aid you in protecting intellectual property rights and ensure user privacy. Here comes the significance of using video encryption.
Table of Contents
ToggleAn Overview of Video Encryption
It is a great way to protect videos published over the internet from unreadable data using encrypted keys.
Let’s discuss with an example-
If you publish a video on entertainment or on any event, then you want to share it with others. On the other hand, if your video is based on corporate training, then you won’t ever make it available to unauthorized users.
Here, if we talk about video encryption, it is a process of securing/protecting videos digitally to avoid unwanted interception and accessing of the transmitted videos from unwanted people and other prying eyes. This process includes encrypted videos with specific hardware setups and specific software for securing your high sensitive digital video content.
Video encryption involves different types of technologies-
- Adaptive streaming
- Line inversion
- Media/device-specific
- Region-specific streaming
- Software-specific video
This method uses keys and algorithms to perform mathematical operations on data efficiently.
Top Techniques of Video Encryption
If you want to make video encrypter more effective and efficient, then you should follow some best practices. It involves picking long key and strong encryption algorithm which are most suitable for security and system requirements. What’s more, you should use different types of keys for
files, streams or cameras. The best part is that you should change keys regularly to avoid key compromise or reuse. In addition to this, you should store and manage keys separately and securely from the data using key management services or tools.
In video encryption, symmetric and asymmetric – two types of methods are used.
- Symmetric encryption is a great process that can encrypt the message using a key and the same key is used for decryption.
- On the contrary, asymmetric encryption method is based on private and public key encryption techniques. This technique uses different keys for encryption and decryption data. However it is relatively secure method than symmetric, but it is slower too.
Apart from this, you can also use hybrid encryption which is a mixture of symmetric and asymmetric key encryption. In today’s date, it is used in all forms of internet communication between server and clients. The best example of hybrid encryption is the SSL handshake.
Key Components of Video Encryption
Encrypted video is considered as the best option if you want to protect your premium videos. The challenging part is to make content keys available to authorized people only. For this, content keys are needed for decryption and playing videos.
Some most common techniques of video encryption are
- AES 128 video encryption
- RTMP streaming
- RTMP encryption (RTMP E)
- HLS streaming & HLS encryption
Let’s check out how Video Encryption works
- Encryption Algorithm Selection- You first need to select the right algorithm for video encryption. The most common encryption algorithms are RSA (Rivest-Shamir-Adleman) and AES (Advanced Encryption Standard).
- Encryption Key Generation – Generate encryption keys using cryptographic algorithms. The overall strength of video encryption totally depends upon the complexity and length of generated keys.
- Encryption – Once you generate keys, you need to convert your data into a scrambled format with encryption algorithms.
- Transmission – Transmit/store your encrypted videos over networks in cipher text format.
- Decryption: In this step, the recipient can convert encrypted video in its original form and enjoy authorized viewing.
Main Challenge of Video Encryption
Video encryption is helpful to protect data and ensure privacy. However, it has some limitations.
Data Hacking & Lack of Tools
In today’s technological advancement era, hackers have become more sophisticated. So, encryption algorithms should be upgraded and strengthened. What’s more, there is no special software to manage and protect encryption keys properly.
In such cases, human errors like using weak passwords or losing track of encryption keys may compromise encrypted data security.
Applications of Video Encryption
When it comes to encryption, it is beneficial for different types of applications across almost all industries, such as
- Event promotions
- Educational institutions
- Training institutes
- News or advertising agencies, and many more.
By using this method, you can not only maintain privacy, but you can also keep your intellectual property protected.
Wrapping Up
To sum up, encrypted video streaming is one of the great tools, letting you to safeguard your videos and more sensitive information. But in this regard, you should use great practices as well as the right methods of video encryption. As technology advances, you will get more effective and advanced encryption methods in future. Hope this blogpost will suffice to gain great insights about video encryption and its techniques!
For more details, you can connect with our experts here.